x509 Certificates & mTLS course
by IloGus - 09/04/2023
Summary
- Introduction
- Cryptography
- x509 certificates
- TP 1: generation of x509 certificates
- TP 2: mTLS connection
- Advanced x509 certificate
Introduction
In this course, I will learn what an x509 certificate is, what a CA is, how to generate certificates, how to set up an mTLS communication.
SSL vs TLS
Let's see what the difference is between SSL and TLS :
SSL and TLS are protocols! They use certificates.
(ANSSI recommends the use of TLS 1.2 and 1.3 only)
Why I still see SSL certificate written?
Historically, certificate providers sold their certificates as: "SSL Certificate".
The name was kept so as not to confuse customers.
Now we can see vendors offering SSL/TLS Certificates
Cryptography reminder
Cryptography:
“The practice of creating and understanding codes that keep information secret.”
Symmetry vs. asymmetry
To understand certificates, you need to understand the principle of symmetric vs. asymmetric encryption.
Symmetry
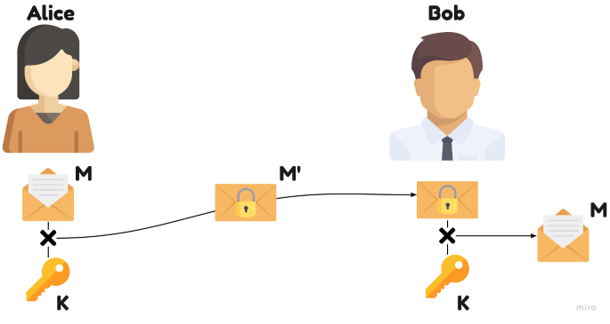
To encrypt the message (M), Alice and Bob use the same key (K) that they both know.
Asymmetry
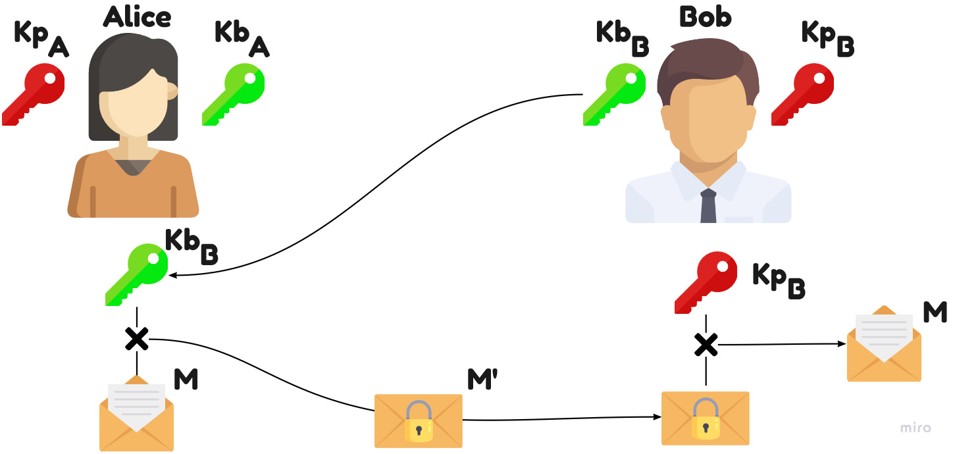
Use of a key pair: a public key, used for encryption. A private key, used for decryption. (It is currently impossible to back out the private key from the public key)
Hash function
“A hash function is any function that can be used to map data of arbitrary size to fixed-size values, though there are some hash functions that support variable length output. The values returned by a hash function are called hash values, hash codes, digests, or simply hashes.”
Asymmetry
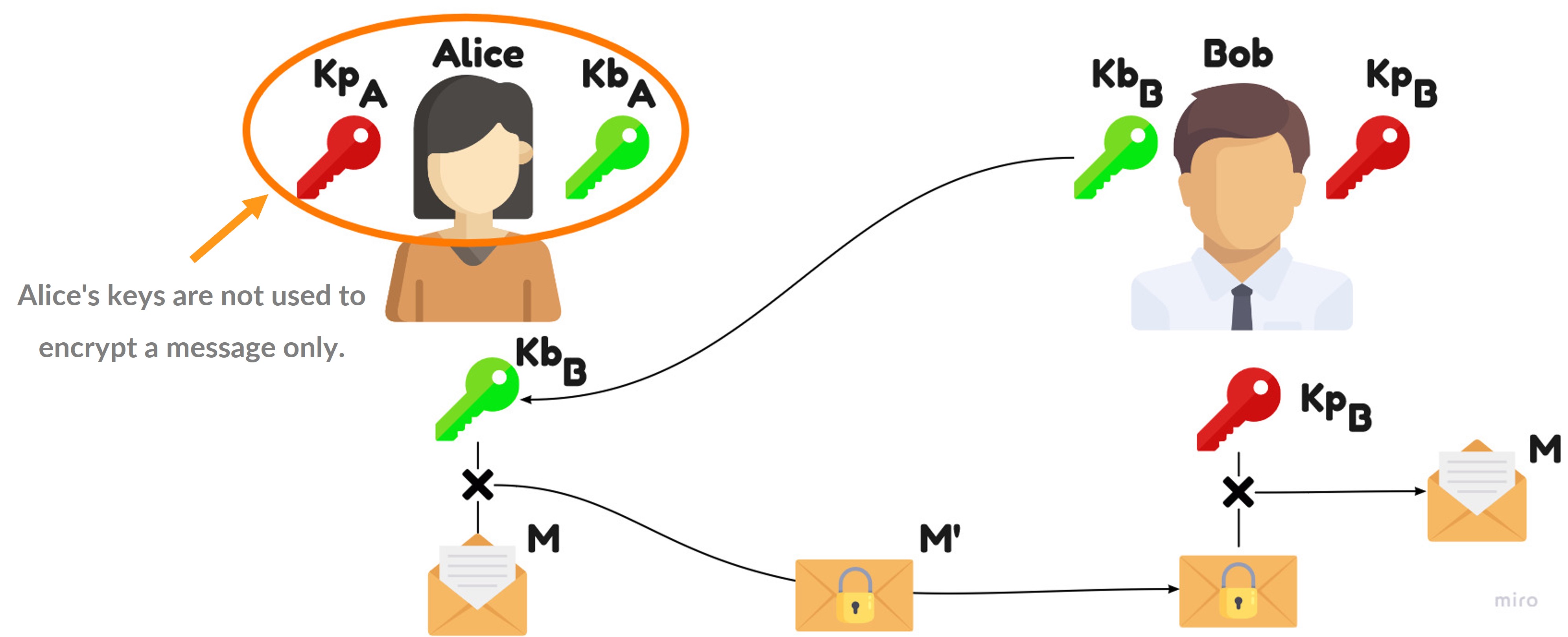
Example: Alice wants to send a encrypted message to Bob, she uses Bob's public key and NOT her own
Asymmetry
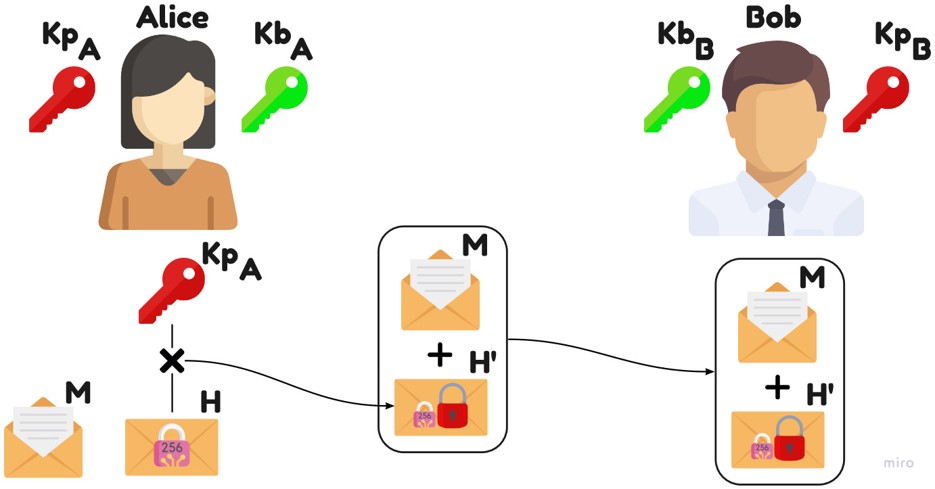
Example: Alice want to signs a message for Bob.
She use her KpA
Asymmetry
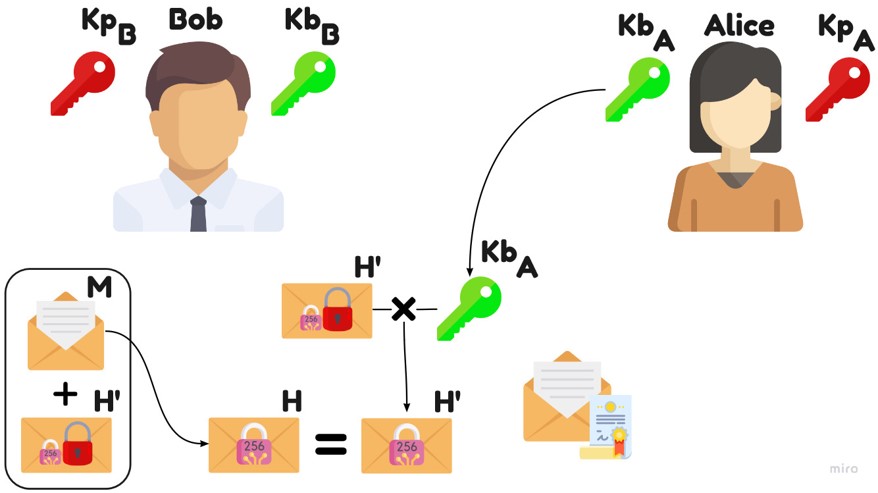
Example: Bob checks/validate Alice's signature.
He use KbA
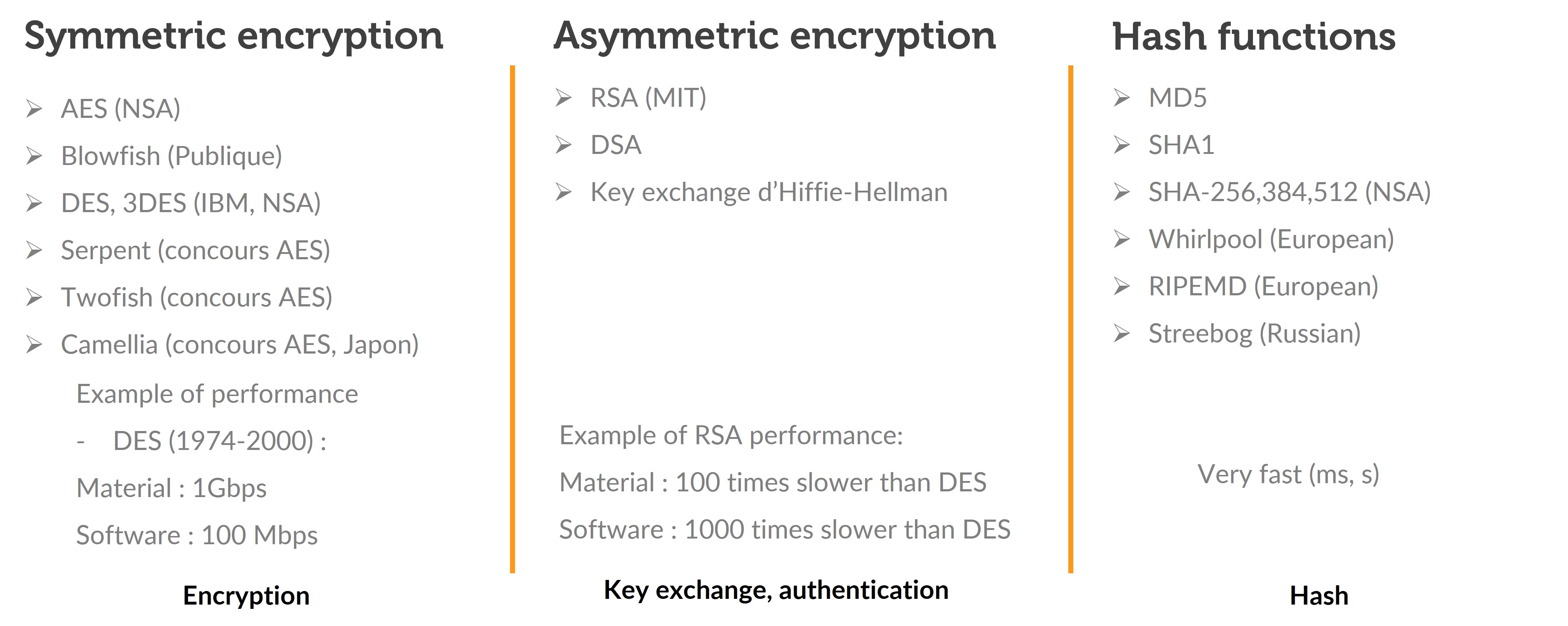
The different algorithms
 More info: https://ciphersuite.info
More info: https://ciphersuite.info
The function of these algorithms
We have seen three categories of algorithm/function. Symmetric algorithms encrypt large amounts of data. Asymmetric algorithms encrypt small amounts of data. Hash functions allow the verification of data.
In a TLS communication, we use different algorithms and we call this a "cryptographic suite".
Example of a cryptographic suite:
TLS_RSA_WITH_AES_128_GCM_SHA256
- Key Exchange : RSA
- Authentication : RSA
- Encryption : AES
- Hash : SHA256
Example on a graph...
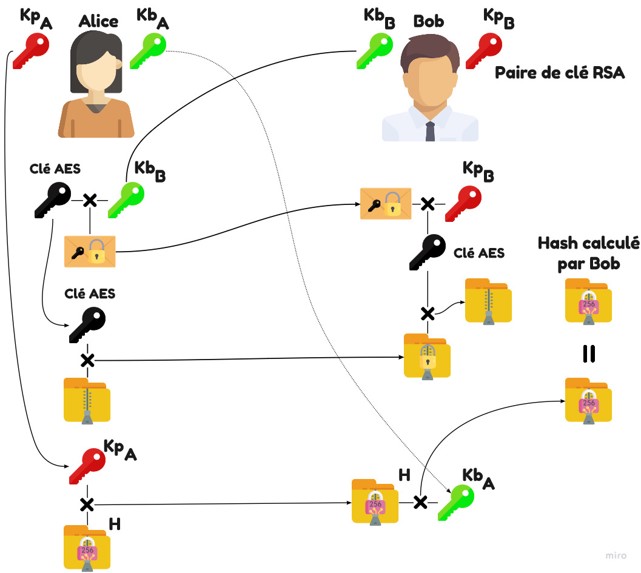
The x509 certificates
Definition
“An X.509 certificate binds an identity to a public key using a digital signature. A certificate contains an identity (a hostname, or an organization, or an individual) and a public key (RSA, DSA, ECDSA, ed25519, etc.), and is either signed by a certificate authority or is self-signed.”
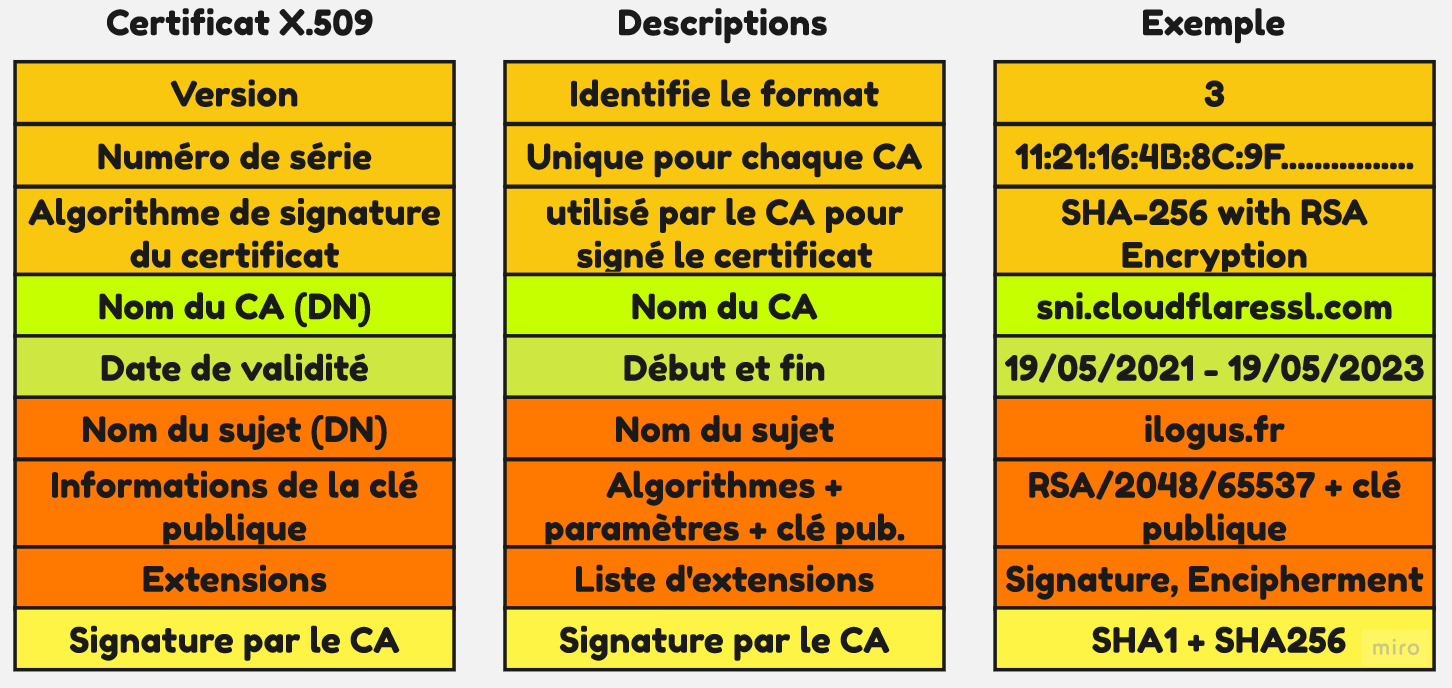
Details of a certificate
What is a Certification Authority (CA)?
The CA guarantees the authenticity of the X509 certificate (relationship: public key, owner) by signing the X.509 certificate with the CA's private key
This certificate can be verified by all thanks to the signature control with the public key of the CA
The role of the CA is to provide a level of confidence in the identification of users based on a PKI.
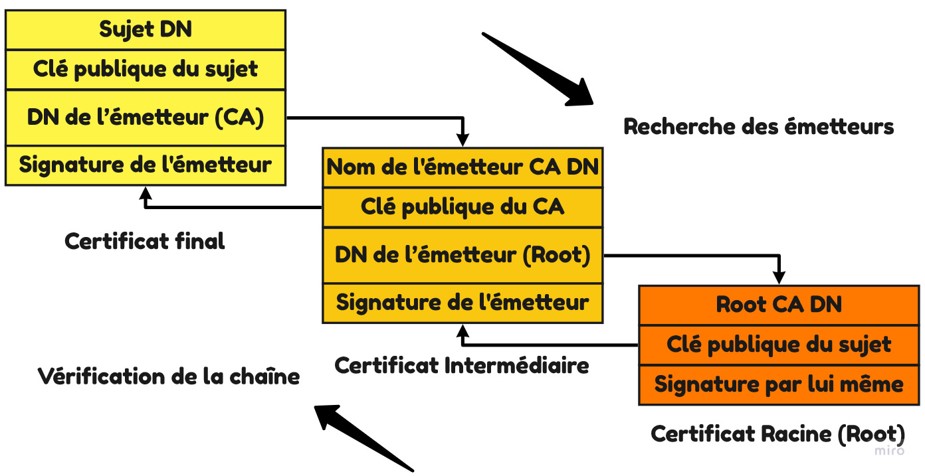
Certificate chain
What is a certificate chain?
We have seen that a certification authority is a certificate we trust. Therefore, we can make a trusted certificate chain.
In this way, our computer or browser stores in a "certificate store" the root certificates we trust.
Certificate chain (theory)
Certificate chain in practice
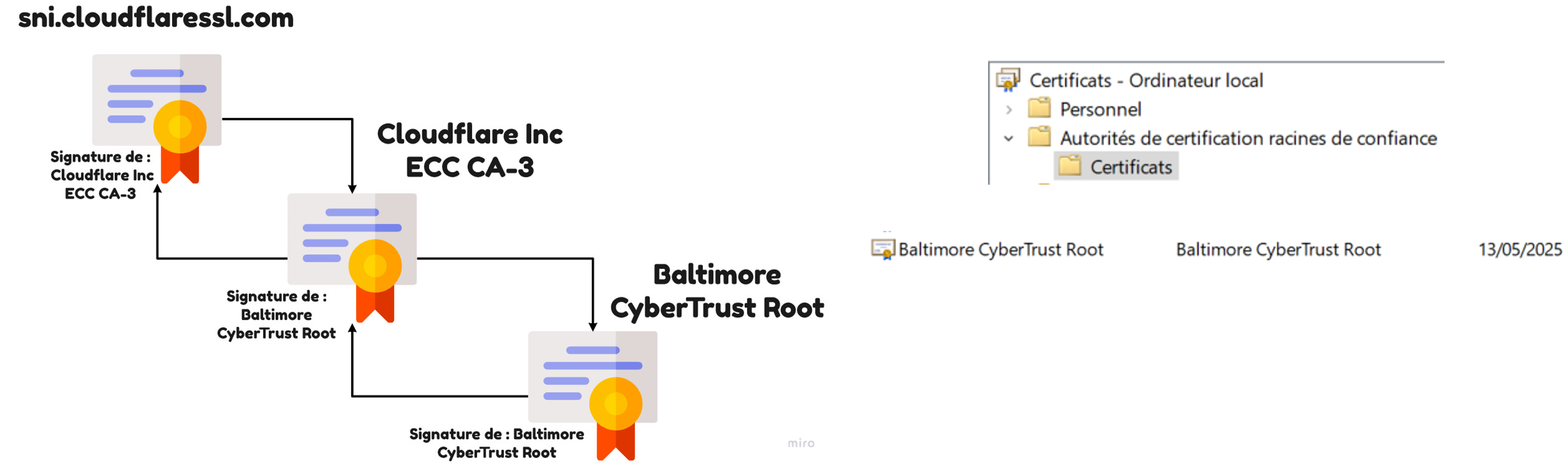
TP1: Generation of certificates
Connect to the test server
In a terminal (cmd/wsl):
ssh [email protected]Joining the screen:
screen -xTo exit the screen use CTRL+A then D:
Generation of the certification authority (CA)
Practice!
Generate the private key of the future CA:
openssl genrsa 4096 > ca.keyGenerate the CA certificate:
openssl req -new -x509 -nodes -days 365000 \
-key ca.key \
-out ca.crtInspect the content of the certificate:
openssl x509 -in ca.crt -textGeneration of a CSR
What is a CSR?
A Certificate Signing Request is a message sent from an applicant to a certificate authority in order to apply for a digital identity certificate. It usually contains the public key for which the certificate should be issued, identifying information (such as a domain name) and a proof of authenticity including integrity protection (e.g., a digital signature).
Practice!
Generate the CSR for the server:
openssl req -newkey rsa:2048 -nodes -days 365 \
-keyout server.key \
-out server.csrInspect the CSR:
cat server.csrGenerate the X509 certificate for the server:
openssl x509 -req -days 365 -CAcreateserial -in server.csr \
-out server.crt -CA ca.crt -CAkey ca.keyInspect the content of the server certificate:
openssl x509 -in server.crt -textPractice!
Generate your own CSR:
(change username with your pseudo)openssl req -newkey rsa:2048 -nodes -days 365 \
-keyout username.key -out username.csrPractice!
Sign the CSR with the CA:
openssl x509 -req -days 365000 -CAcreateserial -in username.csr \
-out username.crt -CA ca.crt -CAkey ca.keyCheck and validate all the:
openssl verify -CAfile ca.crt \
ca.crt \
username.crtTP2: mTLS with postman
Download the certificates
Download your username.crt and username.key and the CA.crt on your computer
Try an http request :
Configure postman to work with certificates
Go to settings, general : disable SSL certificate verification.
Then in certificates, add the CA certificate and your client certificate
Try a https request
Look into the body of the server response, and find the server and client certificates
Wireshark analysis
Perform a http request and look for the result
Then, perform a https request and try to find the client and server certificates
We will repeat with TLSv1, v2 and v3
Advanced x509 certificate
Extended Key Usage
Key usage extensions define the purpose of the public key contained in a certificate. You can use them to restrict the public key to as few or as many operations as needed. For example, if you have a key used only for signing or verifying a signature, enable the digital signature and/or non-repudiation extensions.
hcltechsw.comPractice!
Regenerate the server certificate with :
TLS WWW server authentication
Openssl config file
To be able to indicate to openssl the aspects of our certificate, we will create a configuration file: server.cnf.
Copy the openssl.cnf to server.cnf:
cp /etc/ssl/openssl.cnf server.cnfEdit the req bloc
Inside the server.cnf, edit the req bloc:
[ req ]
distinguished_name = req_distinguished_name
attributes = req_attributes
x509_extensions = v3_ca
req_extensions = v3_req
x509_extensions = usr_certEdit the usr_cert bloc
Inside the server.cnf, edit the usr_cert bloc:
[ usr_cert ]
basicConstraints=CA:FALSE
nsCertType = server
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = serverAuth
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuerEdit the v3_req bloc
Inside the server.cnf, edit the v3_req bloc:
[ v3_req ]
extendedKeyUsage = serverAuth
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEnciphermentGenerate the CSR
Add the server.cnf to the CSR command:
openssl req -config server.cnf -newkey rsa:2048 -nodes -days 365 \
-keyout server.key -out server.csrVerify the CSR:
openssl req -in server.csr -textSign the CSR with the CA:
Add the extensions and extfile to the command:
openssl x509 -req -days 365 -CAcreateserial -in server.csr \
-out server.crt -CA ca.crt -CAkey ca.key \
-extensions usr_cert -extfile server.cnfVerify the server certificate
openssl x509 -in server.crt -textPratice!
Regenerate your certificates by adding
in the extended key usage:
Client authentication, E-mail Protection, TLS client
Create the config file
Copy the server.cnf to username.cnf:
cp server.cnf username.cnfEdit the usr_cert and v3_req bloc:
[ usr_cert ]
nsCertType = client, email
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = clientAuth, emailProtection
[ v3_req ]
extendedKeyUsage = clientAuth, emailProtectionGenerate the CSR and sign it
Generate the CSR:
openssl req -config username.cnf -newkey rsa:2048 -nodes -days 365 \
-keyout username.key -out username.csrSign the CSR:
openssl x509 -req -days 365 -CAcreateserial -in username.csr \
-out username.crt -CA ca.crt -CAkey ca.key \
-extensions usr_cert -extfile username.cnfEmail signing
Combine your crt and key into a p12 file:
openssl pkcs12 -export -out username.pfx \
-inkey username.key -in username.crt